Introduction
Trezor Suite is designed to be a single trusted interface for interacting with your Trezor hardware wallet. Its core principle: private keys and signing authority remain inside the hardware device at all times. The host application (Suite) provides account management, transaction construction, portfolio views, and firmware updates while the device provides the cryptographic root of trust and explicit on-device confirmations.
Getting started — verified installation
Begin at the official onboarding portal and download Trezor Suite for your operating system (Windows, macOS, Linux) or use the secure web app where supported. Always obtain installers from the vendor’s official domain and verify signatures or checksums when provided. After installing Suite, connect your Trezor device with a quality USB cable, unlock it using your PIN, and follow the guided onboarding flow to initialize or restore a wallet.
Do not use devices that arrive pre-configured. If your device shows unexpected prompts during first use, contact verified support before proceeding.
Initialization & recovery seed best practices
When a Trezor device is initialized, it generates a recovery seed (typically 12–24 words) directly on-device. Write this seed down physically on an offline medium and store copies in secure, geographically separated locations. Consider metal backup plates for fire/water resistance. Never photograph, type, or store the seed in cloud services. Treat any request for your seed as a high-probability scam.
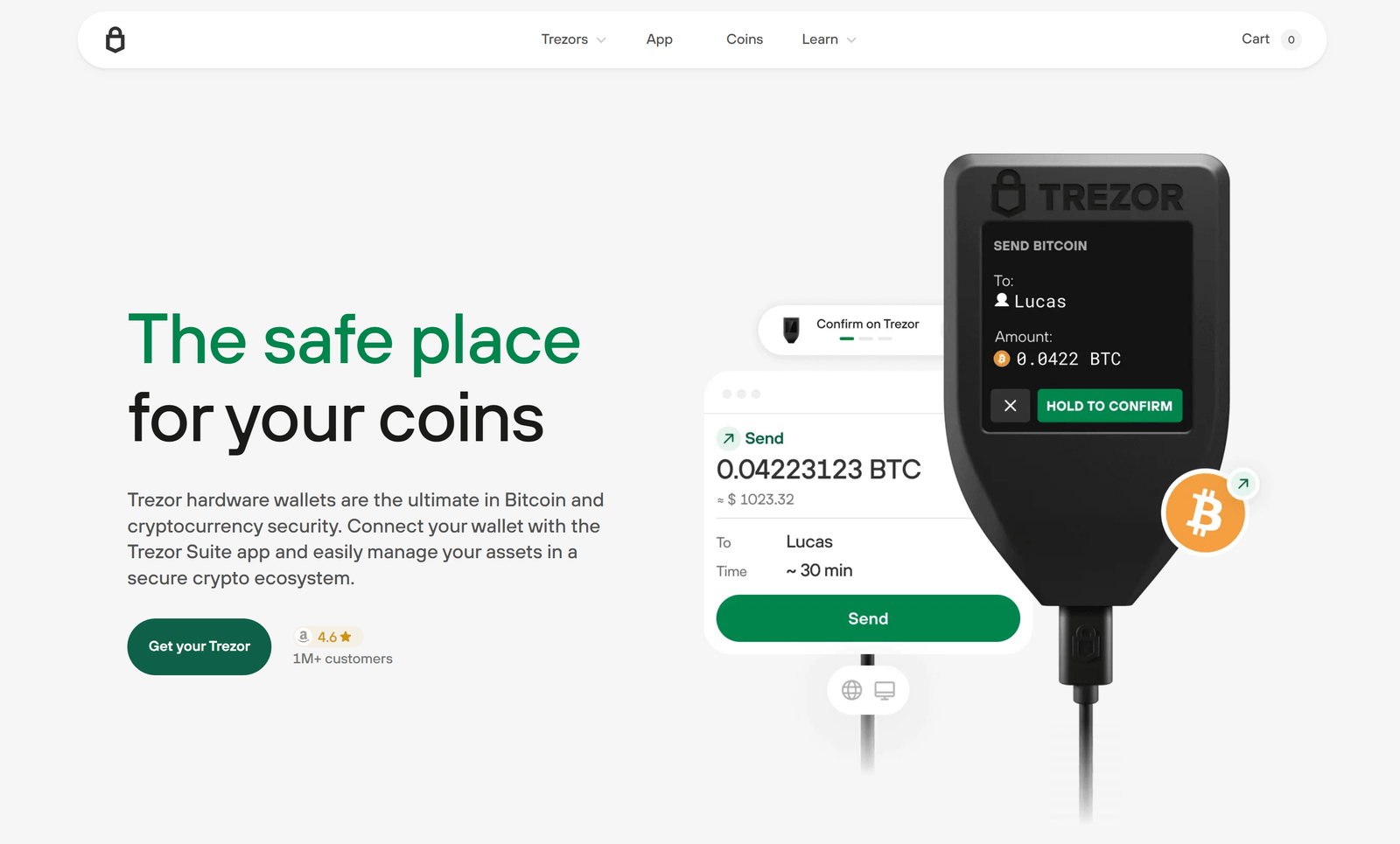
Core features & user workflow
Trezor Suite provides account aggregation, transaction tools, portfolio analytics, swap/exchange integrations, and support for NFTs and staking where applicable. Typical workflow:
- Install chain-specific apps on your device via Suite’s Manager (minimal necessary apps recommended).
- Add accounts in Suite to view balances and history.
- Construct transactions inside Suite; verify recipient, amount and fees on-device.
- Sign transactions on-device — private keys never leave the secure element.
Firmware & application updates
Firmware updates are published to improve security and add features. Suite will prompt when a signed firmware update is available. Apply updates only through the official Suite flow — updates require on-device confirmation which prevents silent or unauthorized firmware changes. Always back up your recovery seed before major updates and ensure your host environment is trusted and malware-free.
Privacy & telemetry
Trezor Suite aims to minimize data collection and offers options to disable telemetry. Account and transaction data are stored locally; Suite will not post private keys to remote servers. For enhanced network privacy, advanced users can route Suite traffic via privacy tools (VPNs, Tor) or run dedicated nodes. Coin-control and address hygiene reduce on-chain linkability.
Troubleshooting
Common issues include device detection and USB connectivity. Steps to resolve: try a different USB cable and port (prefer direct ports), restart Suite and device, confirm that Bridge or required helper services are running, and reinstall Suite from the official site if needed. For persistent problems, consult official documentation and verified support — never share your recovery seed with support personnel.
Advanced & enterprise considerations
Organizations should pair Trezor devices with hardened endpoints, multi-signature architectures, strict provisioning logs, and internal custody playbooks. Centralized update management, signed distributions, and clear separation of duties reduce insider risks. Combine hardware wallets with multi-sig to avoid single points of failure for high-value custody.
Trezor Suite balances usability with robust security. Whether you are protecting a small personal portfolio or designing an institutional custody policy, the Suite + device model enforces that keys remain cryptographically isolated while giving you a clear, auditable operational experience.